Mapping Network Drives with the net use Command: A Comprehensive Guide
Related Articles: Mapping Network Drives with the net use Command: A Comprehensive Guide
Introduction
In this auspicious occasion, we are delighted to delve into the intriguing topic related to Mapping Network Drives with the net use Command: A Comprehensive Guide. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
- 1 Related Articles: Mapping Network Drives with the net use Command: A Comprehensive Guide
- 2 Introduction
- 3 Mapping Network Drives with the net use Command: A Comprehensive Guide
- 3.1 Understanding the net use Command: A Foundation for Network Connectivity
- 3.2 Syntax and Essential Parameters: Decoding the net use Command
- 3.3 Navigating the Landscape of net use Options: A Deeper Dive
- 3.4 Practical Applications: Harnessing the Power of net use
- 3.5 Security Considerations: Safeguarding Network Access
- 3.6 Troubleshooting Common Issues: Resolving net use Challenges
- 3.7 Frequently Asked Questions: Clarifying Common Concerns
- 3.8 Tips for Effective Network Drive Mapping: Best Practices
- 3.9 Conclusion: Empowering Network Access with net use
- 4 Closure
Mapping Network Drives with the net use Command: A Comprehensive Guide
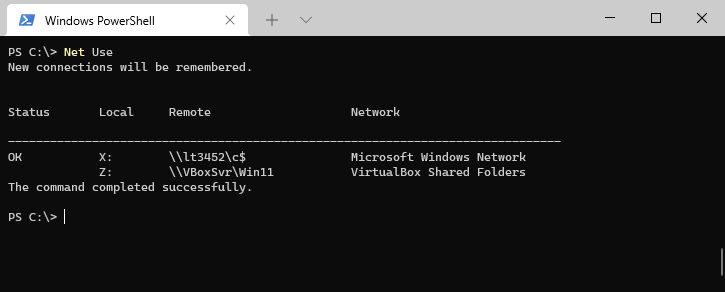
In the realm of network administration, the ability to access shared resources efficiently is paramount. This is where the net use command, a powerful tool available in Windows operating systems, comes into play. It empowers users to establish connections to network drives, seamlessly integrating remote resources into their local system. This guide delves into the intricacies of the net use command, exploring its various functionalities, syntax, and practical applications.
Understanding the net use Command: A Foundation for Network Connectivity
The net use command serves as a bridge between local computers and network shares, facilitating access to shared files, folders, and printers. Its core function is to map a local drive letter to a network resource, enabling users to navigate and interact with the remote share as if it were a local drive. This simplification streamlines file access, promoting efficiency and ease of use.
Syntax and Essential Parameters: Decoding the net use Command
The net use command follows a specific syntax, allowing for precise control over the mapping process. Here’s a breakdown of the key parameters:
Basic Syntax:
net use [drive letter:] [servershare] [password] [/user:[domainusername]]Parameters:
-
drive letter:: Specifies the local drive letter to be assigned to the network share. For example,Z:. -
servershare: Identifies the network share, including the server name and the shared resource name. For instance,fileserverdocuments. -
password: Provides the password required to access the network share (optional). -
/user:[domainusername]: Specifies the domain and username to use for authentication (optional).
Example:
net use Z: fileserverdocuments /user:domainusername passwordThis command maps the local drive letter Z: to the network share fileserverdocuments, using the credentials domainusername and password.
Navigating the Landscape of net use Options: A Deeper Dive
The net use command offers a range of options to customize the mapping process. These options enhance flexibility and cater to specific requirements.
Common Options:
-
/persistent:yes: Makes the connection persistent, meaning it will be re-established automatically after a system restart. -
/delete: Removes an existing network drive mapping. -
/home: Maps the user’s home directory on the network share. -
/savecred: Saves the password for future connections. -
/smartcard: Uses a smart card for authentication.
Example:
net use Z: fileserverdocuments /persistent:yesThis command maps the local drive letter Z: to the network share fileserverdocuments and makes the connection persistent.
Practical Applications: Harnessing the Power of net use
The net use command finds widespread application in various scenarios, streamlining network access and improving operational efficiency.
Key Use Cases:
- Accessing Shared Files and Folders: Simplifies the process of accessing and managing files located on network shares.
- Connecting to Remote Printers: Enables seamless printing to shared printers on the network.
- Centralized Data Storage: Facilitates access to shared data repositories, fostering collaboration and data consistency.
- Remote Desktop Access: Creates connections to remote desktops, enabling users to work from different locations.
- Network Administration: Provides a powerful tool for administrators to manage network shares and user permissions.
Security Considerations: Safeguarding Network Access
While the net use command offers convenience, it’s crucial to prioritize security to prevent unauthorized access.
Security Best Practices:
- Strong Passwords: Utilize robust passwords for network shares and accounts.
- Access Control Lists (ACLs): Implement ACLs to restrict access to specific users or groups.
- Password Policies: Enforce strong password policies for network accounts.
- Regular Security Audits: Conduct periodic security audits to identify and address vulnerabilities.
- Multi-Factor Authentication: Employ multi-factor authentication for enhanced security.
Troubleshooting Common Issues: Resolving net use Challenges
Despite its ease of use, net use can sometimes encounter issues. Understanding common problems and their solutions is essential for smooth operation.
Common Errors:
- Incorrect Credentials: Verify username, password, and domain.
- Network Connectivity Issues: Check network connection and server availability.
- Share Permissions: Ensure the user has sufficient permissions to access the share.
- Drive Letter Conflicts: Use a different drive letter if the desired one is already in use.
- Missing Network Drive: Verify the share path and server name.
Troubleshooting Tips:
-
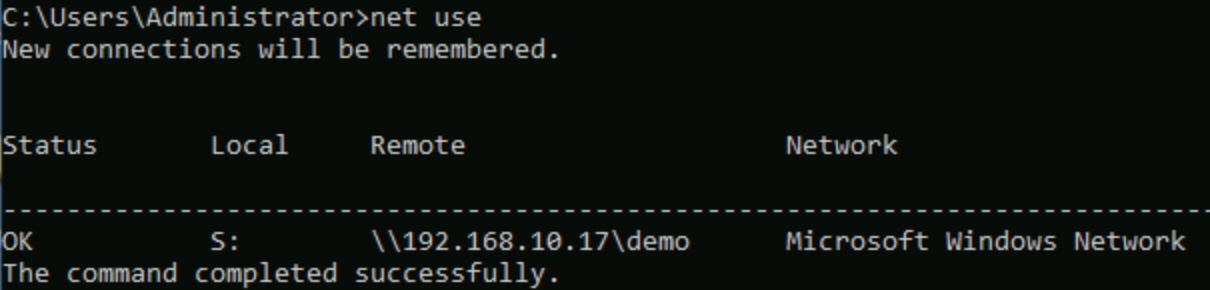
Check Network Connectivity: Use the
pingcommand to test network connectivity to the server. -
Verify Share Permissions: Use the
net sharecommand to check share permissions. -
Check Drive Letter Availability: Use the
net usecommand without parameters to list existing connections. -
Review Event Logs: Analyze system event logs for error messages related to
net use.
Frequently Asked Questions: Clarifying Common Concerns
1. What is the difference between net use and subst?
The net use command establishes a persistent connection to a network share, while the subst command creates a symbolic link, which is a temporary connection.
2. How do I disconnect a network drive mapped with net use?
Use the net use [drive letter:] /delete command to disconnect the drive.
3. Can I use net use to access a remote computer’s desktop?
Yes, the net use command can be used to access a remote desktop using the serveradmin$ share.
4. How do I make a network drive mapping persistent?
Use the /persistent:yes option with the net use command.
5. Can I use net use with a different domain account?
Yes, use the /user:[domainusername] option to specify a different domain account.
Tips for Effective Network Drive Mapping: Best Practices
- Use Descriptive Drive Letters: Assign drive letters that reflect the purpose of the network share.
- Document Connections: Maintain a record of network drive mappings for easy reference.
- Regularly Review Connections: Periodically check and update network drive mappings as needed.
- Utilize Group Policies: Implement group policies to automatically map network drives for users.
- Optimize Performance: Consider using faster network protocols like SMB3 for improved data transfer rates.
Conclusion: Empowering Network Access with net use
The net use command serves as a cornerstone of network administration, providing a streamlined and efficient way to access shared resources. By understanding its syntax, options, and best practices, users can leverage this powerful tool to optimize network connectivity, enhance collaboration, and simplify file management. Implementing robust security measures and troubleshooting potential issues ensures smooth and secure network access, empowering users to maximize the benefits of shared resources.

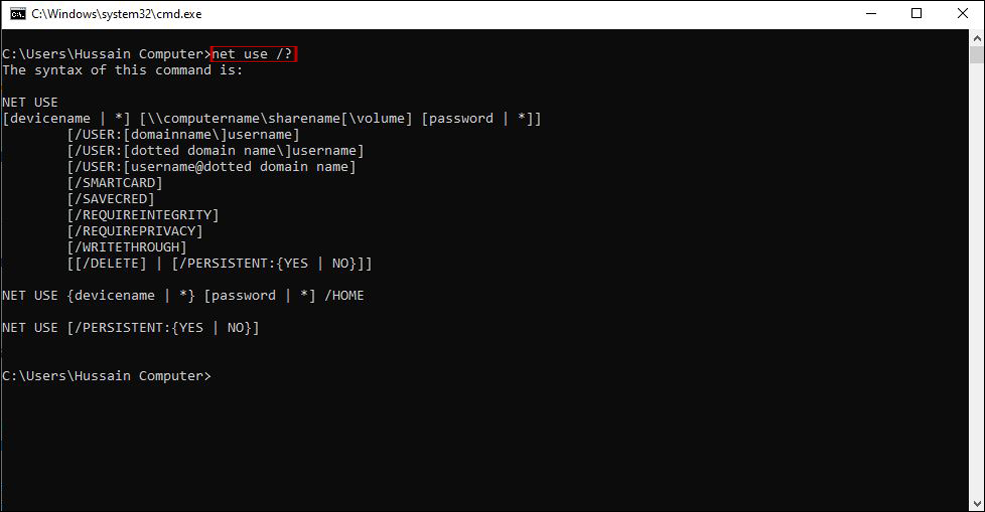
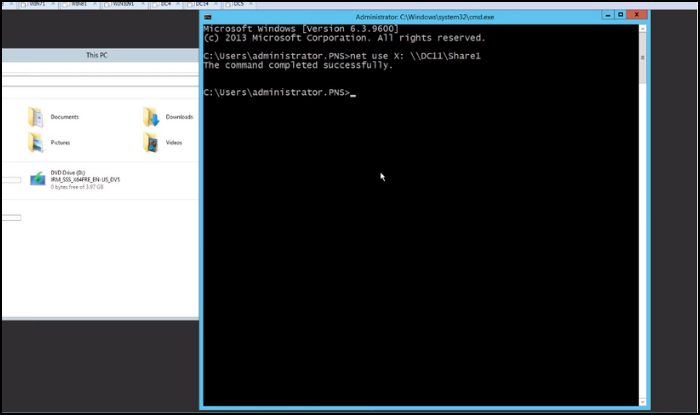



Closure
Thus, we hope this article has provided valuable insights into Mapping Network Drives with the net use Command: A Comprehensive Guide. We hope you find this article informative and beneficial. See you in our next article!